Next-Gen WAF
API protection
Average cost
BUSINESSES MOST AT RISK
Whether or not your industry is on this list, all companies are at risk of data theft.
You need the full-spectrum protection that WAAP solutions provide
Protect against API-specific attacks.
Don't worry about organizational risks. Your API endpoints are securely protected.
Protect against credential stuffing, account takeover (ATO), and brute-force attacks.
Stopping behavior-based attacks by checking and matching query sequences. And intelligent rate limiting to prevent botnets from overloading your resources.
Virtual patching.
Eliminate the risks of malicious exposure to zero-day attacks by patching found vulnerabilities.
Why businesses need web security
Growing attack surface
With the growth of online business, especially in the wake of the COVID-19 global pandemic, the number of web applications and websites that exist is growing exponentially. As the online economy increases, so do the number of web attacks.
Sensitive data protection
Keeping customers' personal, financial, and health data requires companies to take a serious approach to their data security.
Focused protection
OWASP Top-10 risks and other advanced threats are on the rise, requiring a modern NG-WAF to mitigate organizational risk.
API abuse prevention
Automated behavioral attacks—such as malicious bots and application layer (L7) DDoS—are increasing. This can lead to ATO and carding attacks, disrupting end-user experience and putting business-critical services at risk.
How WAAP works
Scans incoming traffic in real time
Verifies traffic according to an existing rule set
Score request validity based on the set weights
Blocks requests if their total score exceeds the threshold
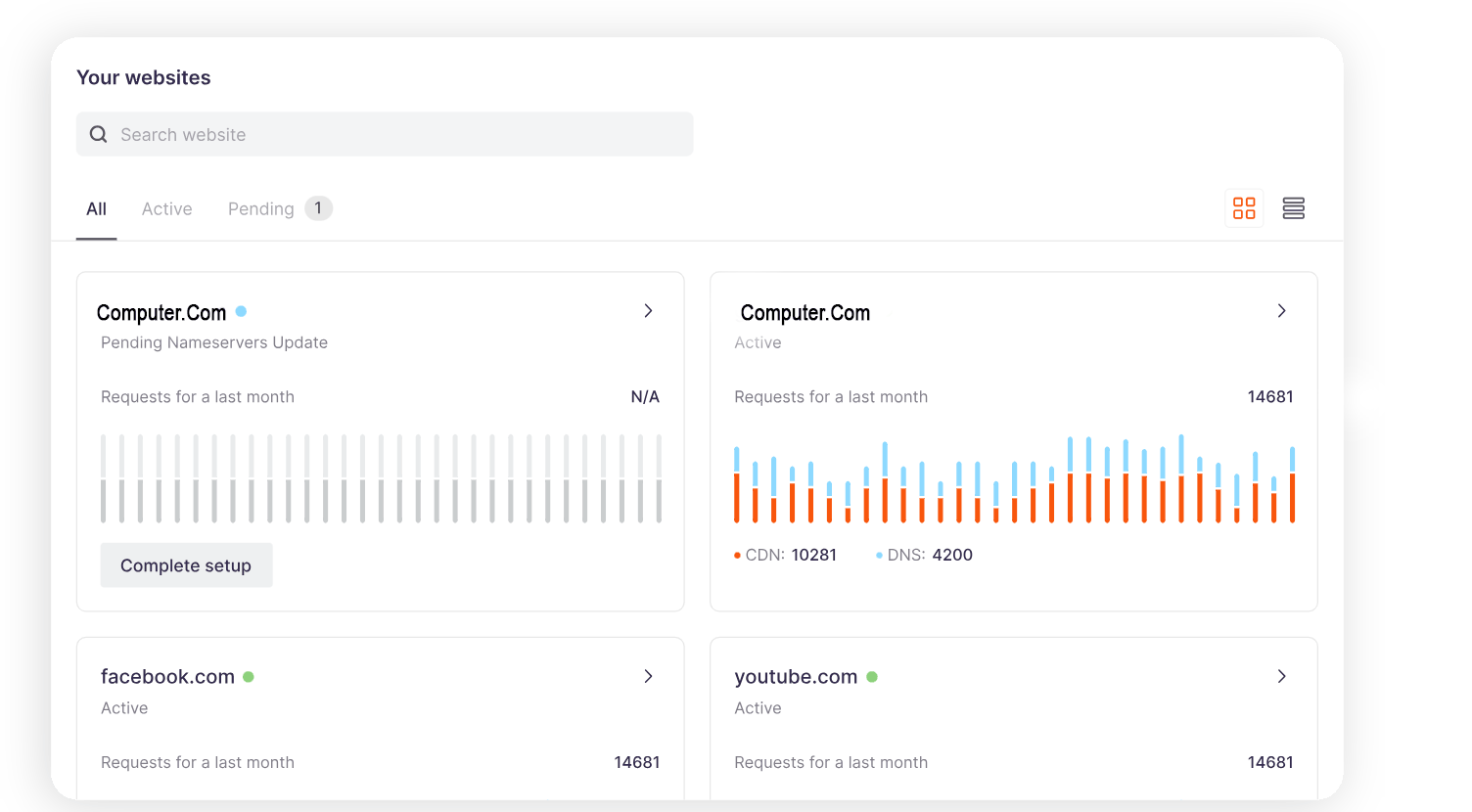
A simple way to control Computer.Com's services
WAAP advantages
Protects against common threats beyond OWASP Top-10 for full coverage against emerging threats: account takeover (ATO), malicious bots, L7 DDoS, and exploitation of 0-day vulnerabilities
01
Detects and fight zero-day attacks using ML technologies
02
Tracks and blocks the use of stolen and disclosed credentials
03
Scans resources to detect potential vulnerabilities
04
Near-zero false positives
05
Fast deployment in any environment and easy management
06
Web application and API protection (WAAP) in any customer environment
07
Automated rulesets based on actual traffic provide business-specific security
08
Stay informed in real time with alerts and triggers
09
Near-zero latency minimizes impact on users while delivering the protection they expect

